Ucam by IoTeX: The Privacy & Security You Need
In this blog, we share how Wyze’s poor handling of user data lead to a wide scale data leak and how the hacks of Ring and Nest cameras happened, as well as how Ucam by IoTeX utilizes blockchain technology to provide the privacy and security that addresses these exploits directly.


As our world becomes more connected, the need for security and privacy has never been greater. While many of us are conscious of hacks to our digital data, the problem really hits home when hacks begin to affect the physical wellbeing of our families. The startling hacks of Ring and Nest, as well as the recent Wyze data breach, have shook the consumer IoT industry to its core, as summed up by a scathing article from the Washington Post:
“Software designed to help people break into websites and devices has gotten so easy to use that it’s practically child’s play, and many companies, including Nest, have effectively chosen to let some hackers slip through the cracks.”
These attacks which exposed countless user devices and data to hackers are the direct result of insufficient emphasis on security and privacy. In contrast, IoTeX believes in prioritizing security and privacy above all else— we built Ucam to prevent these types of attacks and give users full control over their data, identity, and privacy.
In this blog, we share how Wyze’s poor handling of user data lead to a wide scale data leak and how the hacks of Ring and Nest cameras happened, as well as how Ucam by IoTeX utilizes blockchain technology to provide the privacy and security that addresses these exploits directly.
How Mass Data Breaches Happen
A large-scale mismanagement of user data by Wyze, a popular home security camera brand, exposed sensitive data and account information from 2.4 million users in December 2019. Follow-up research indicates the error occurred due to employee negligence, where a Cloud admin failed to secure user data after it was transferred to a testing server in order to conduct consumer behavioral testing.
The Wyze data-leak is a perfect example of how traditional business goals directly misalign with the benefits to users. The server transfer was made in order to increase the speed at which business metrics (read: private user data) could be tracked and analyzed. To put a fine point on it, the leakage was only possible because Wyze owned and held user data centrally instead of data being owned (and authorized with permission) by consumers. In fact, the Wyze exposure was far worse than a hack. The data leakage resulted from an open door in Wyze’s servers, as opposed to a clever hacker finding a creative way in to an otherwise secure database.
Wyze is surely not the only consumer-facing company operating in such a way; in fact, this is standard operating procedure. Luckily, we are entering into a new era where it is possible to offer consumers full privacy and great user experience. At IoTeX, we do not even collect user data in the first place, so the Wyze disaster is architecturally impossible. This is the core of IoTeX’s mission — to deliver affordable, functional, and user-centric products to the mass market, where users are the ones with full control of their data.
How Nest & Ring Security Cameras Get Hacked
Device-level hacks have produced incredibly shocking yet relatable headlines lately. These types of hacks grant hackers full access to a device, allowing them to do everything the device owner can do. For example, intruders behind the notorious Nest hack, cited by the Washington Post, played sounds from a pornographic video into the room of a young girl through the family’s Nest camera. Creepy? Yes. Invasive? Of course. Preventable? Absolutely.
How do these hacks originate? Surprisingly, these are not very sophisticated hacks, generally stemming from hackers either brute force hacking or obtaining previously breached logins (i.e., username/password). Brute force hacks are exactly what they sound like — hackers write scripts to guess your password (note: today, a 7-digit alphanumeric password can be cracked in under 2 seconds). A more roundabout way passwords are exposed is via cross-pollination of username/password combos (i.e., your “Internet Identity”) for websites, apps, and devices — when one source gets breached, hackers purchase the database of logins from the dark web and mass login to Nest, Ring, and other IoT devices to wreak havoc on unsuspecting people.
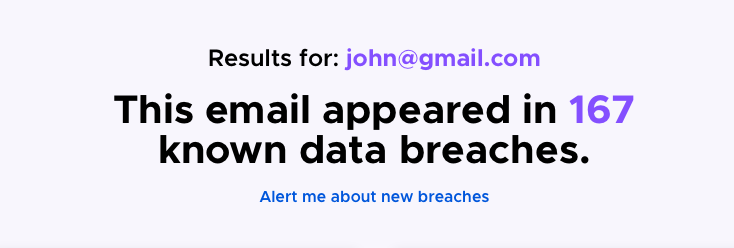
Almost every regular Internet user has had at least one of their passwords leaked in an online data breach. See if you have been the victim of a data breach by checking your email address using this tool from Mozilla.
In response to the recent Nest hacks, Google skirted responsibility by blaming users for failing to use unique passwords when setting up their devices. At IoTeX, we believe that trillion dollar companies shouldn’t blame users for failing to properly secure their devices — rather, proper security and privacy frameworks should be built into IoT devices out-of-the-box.
How Ucam Uses Blockchain to Provide the Security & Privacy You Need
In the midst of recent headlines that have damaged consumer trust in IoT devices, especially home security cameras, IoTeX is determined to introduce an entirely new class of “Powered by IoTeX” devices that exhibit enhanced security, are built on user-centric philosophy, and provide full consumer data ownership and privacy. To accomplish this, IoTeX utilized blockchain in the design of Ucam for two crucial purposes:
- Secure Blockchain Identity & Login, which is not brute force hackable and separate from one’s “Internet Identity”
- Decentralized Issuance of Encryption Keys, to ensure users are the only ones with access to their data, identity, and privacy
The first way Ucam uses blockchain is for one-click setup to create a secure IoTeX blockchain identity (i.e., public/private key pair) for the user. Unlike traditional app/device logins, blockchain public/private keys are impossible to brute force hack. Furthermore, this public/private key pair is unique from all other username/password combos (“Internet Identity”) used to login to websites and apps. This application of blockchain-based identity is an important consumer safeguard, and will greatly mitigate the largest sources of device-level security camera hacks described in the above section.
Note: security is a never-ending challenge. As new security safeguards are implemented, hackers are always creating new paths to access our devices and data. We highly recommend our community to utilize best practices to prevent emerging password, network, and social engineering attacks.
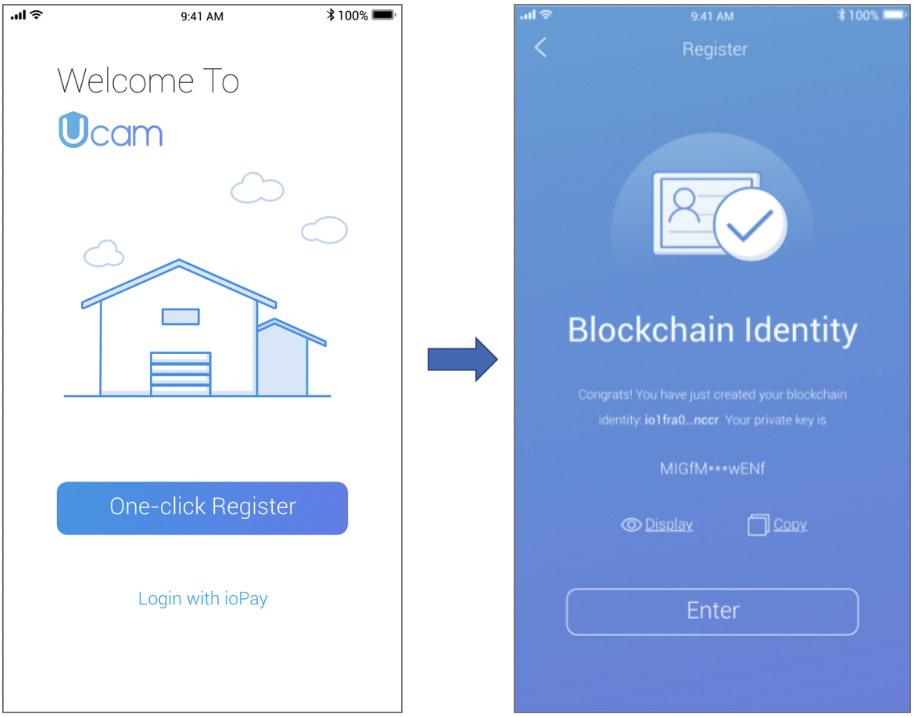
The second way Ucam uses blockchain is to issue encryption keys to Ucam owners in a decentralized fashion. Today, centralized corporations are the ones that create encryption keys, providing one copy to the user and holding a copy for themselves. Mismanagement of users’ data under the supervision of centralized corporations has left mass amounts of sensitive personal information exposed on the dark web. It’s time to adopt devices that we know work for us, not for corporations.
With Ucam, YOU and only YOU are the sole owner of the encryption key and the only one that can access your data — not IoTeX, not Tenvis, not Cloud providers, not anyone! Ucam’s decentralized issuance of encryption keys is coupled with other technological innovations, such as built-in edge computing capabilities, to provide users with full data privacy and comprehensive features.
Unlike other Cloud-based cameras, all processing (e.g., encryption, motion detection, two-way audio) is performed “on the edge”. This removes the need to use a centralized Cloud to store/compute data — all critical computation is performed directly on the Ucam device or user’s mobile phone. As a result, falling victim to mass data breaches as a result of corporate negligence is simply not possible. With Ucam, you are fully in control of your data, identity, and privacy.
For more details on Ucam, please visit https://iotex.io/ucam.
About IoTeX
Founded as an open source platform in 2017, IoTeX is building the Internet of Trusted Things, where all physical and virtual “things” — humans, machines, businesses, and DApps — can exchange information and value at global scale.
Backed by a global team of 30+ top research scientists and engineers, IoTeX combines blockchain, secure hardware, and decentralized identity to empower intelligent IoT networks and machine economies. By serving as a decentralized trust fabric for IoT, IoTeX will empower the future decentralized world by “connecting the physical world, block by block”.
